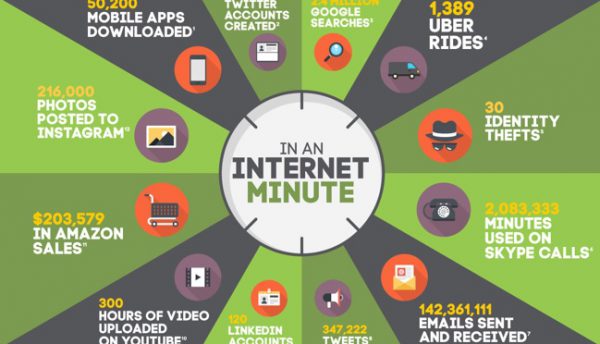
Can you afford $500 per minute of internet downtime?
Many organisations have no clue how much one minute of internet downtime costs them, or haven’t stopped to think about it, says Tom Beinkowski, Director of Product Marketing at Arbor Networks. As a result, they greatly u...