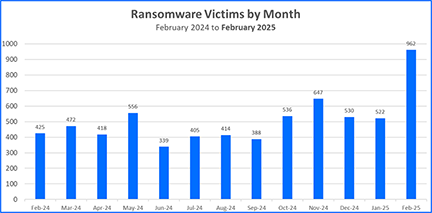
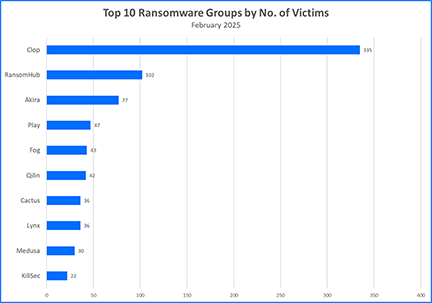
In the latest Bitdefender Threat Debrief February is revealed as a grim milestone in ransomware history: with a staggering 126% increase of claimed victims year-over-year, jumping from 425 victims in February 2024 to 962 in February 2025. This is the single worst month in ransomware history based on the total number of claimed victims. Of those 962 victims, a staggering 335 were claimed by the Clop (Cl0p) group. That’s a 300% jump from the previous month by this RaaS (Ransomware-as-a-Service) group. It begs the question: what’s behind this sudden spike?
The answer lies in a shift Bitdefender have been warning about since 2022 that is still catching many by surprise. Instead of focusing on specific companies or industries, some ransomware groups are becoming increasingly opportunistic by targeting newly discovered software vulnerabilities in edge network devices.
Cybercriminals, regardless of whether they’re financially motivated or state-affiliated, focus on finding vulnerabilities that meet certain criteria:
• The vulnerabilities have high-risk scores (CVSS).
• The vulnerabilities allow attackers to remotely take control of a system (RCE).
• The vulnerabilities affect software that’s accessible from the Internet.
• An exploit developer or malicious actor has already published the proof of concept (PoC) for the exploitation process.
In less than 24 hours of the vulnerability’s public disclosure, threat actors launch automated scanners that scan the Internet and establish remote access to vulnerable systems. After this initial access blitz comes the second stage of the attack – the manual hacking of the victims. This second stage takes time.
Attackers need to figure out which systems are worth their effort, and then they have to manually hack their way deeper, typically using living off the land techniques to evade detection. This delay means the actual ransomware attack or data theft typically happens weeks or even months later.
In Cl0p’s case, Bitdefender’s analysis points to their exploitation of two recent vulnerabilities in Cleo file transfer software, CVE-2024-50623 and CVE-2024-55956. These vulnerabilities, rated 9.8 out of 10 in severity, allowed attackers to run commands on vulnerable systems. Even though these vulnerabilities were revealed in October and December 2024, the manual part of the attack is what takes time, which can explain why we are seeing these victims now.
Here are a few key defences that can make a significant difference:
• Smart Patching: Prioritise patches for actively exploited vulnerabilities and maintain awareness of known exploits (CISA KEV catalogue). A flexible patching strategy is key to rapid response.
• Threat Hunting: Proactively search your network for hidden threats. Discover backdoors before attackers launch their main attack.
• EDR/XDR with SOC/MDR: Use advanced detection systems (EDR/XDR) and expert analysis (SOC/MDR) to detect attackers moving within your network (lateral movement) and stop them before they reach critical data.