Positive Technologies has revealed hackers are increasingly flaunting their successful attacks and giving away stolen data on the dark web
Positive Technologies has unveiled comprehensive research on the shadow market of cybercriminal services targeting the Gulf countries. The UAE and Saudi Arabian organisations remain in the crosshairs of cybercriminals, and over half of all posts on darknet forums are about selling data and access to local companies’ infrastructures.
Researchers have highlighted a sharp increase in the free distribution of such data on the dark web, along with a surge in reports of DDoS attacks targeting the public sector and other industries.
One-in-five ads analysed was related to buying or selling access, with two-thirds available for under US$1,000.
According to the research, cybercriminals remain focused on the two largest economies in the region – the UAE (40% of all posts) and Saudi Arabia (26%).
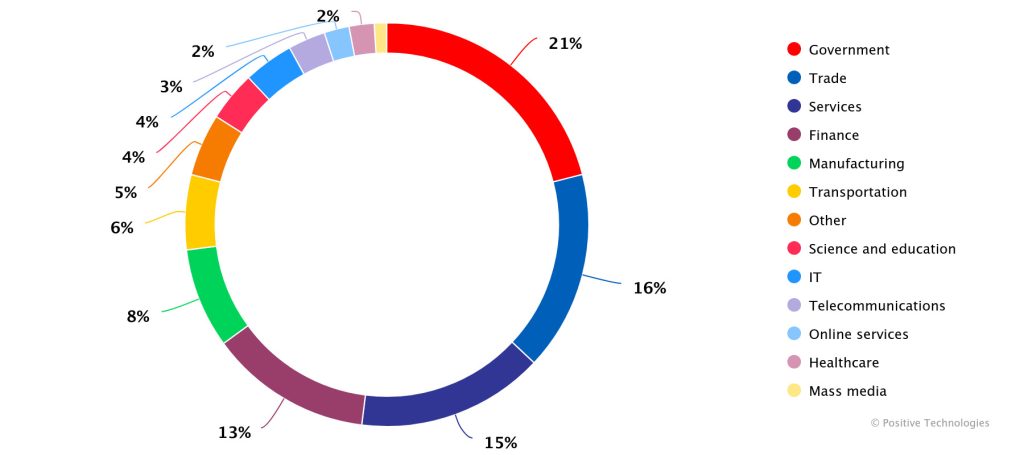
The spotlight on darknet forums is on the public sector, which accounted for 21% of all analysed posts. Most of the data (63%) related to regional government institutions was published for free as part of hacktivist attacks. Next in line for most popular on the dark web are commerce (16% of all ads), the service sector (15%) and financial institutions (13%).
Amid geopolitical tensions, hacker groups have ramped up calls for DDoS attacks and breaches to disrupt government institutions in the region. In the first half of 2024, the number of reports on the results of DDoS attacks on the dark web surged by 70% compared to the same period in 2023. Beyond the public sector, hacktivists also targeted the financial and transportation sectors.
According to the research, 33% of all the analysed ads were linked to data breaches. One-third of these messages were about selling information, and in these ads, criminals primarily offered databases stolen from major commerce companies, with an average cost of US$2,300.
Positive Technologies Analyst, Anastasiya Chursina, said: “When compared to our previous research over a similar period, the share of freely distributed data almost doubled (up to 59%). This allows criminals to broaden the profiles of potential victims for targeted attacks. If the victim refuses to pay the ransom, both ransomware groups and hacktivists (whose goal is to draw public attention to a political stance rather than just receive financial gain) can distribute data for free.”
The vast amount of access-for-sale ads on the darknet and their low cost make it easier for cybercriminals to gain initial access and launch attacks on organisations in the region.
Positive Technologies recommends that companies build their defences based on result-driven cybersecurity, using modern tools such as application-level firewalls (PT Application Firewall), including cloud versions (PT Cloud Application Firewall), network traffic analysis systems (for example, PT Network Attack Discovery), solutions for monitoring information security events and managing incidents (MaxPatrol SIEM), as well as metaproducts (MaxPatrol O2).



