Saeed Abbasi, Product Manager, Vulnerability Research, Qualys Threat Research Unit (TRU), tells us the escalating threat of ransomware in the Arab Gulf region, with Saudi Arabia and the GCC being heavily targeted.

In the Arab Gulf region, ransomware has become an epidemic. Since 2019, Saudi Arabia has been a top target for RansomOps gangs.
The GCC remained the most affected territory in the Middle East and Africa, as of 2023, showing a 65% increase over 2022 for instances of victims’ information being posted to data-leak sites. According to the Known Exploited Vulnerabilities (KEV) catalog, maintained by the Cybersecurity and Infrastructure Security Agency (CISA) under the US Department of Homeland Security, approximately 20% of the 1,117 exploited vulnerabilities are linked to known ransomware campaigns. Attackers have become more relentless and more sophisticated, just as regional security teams have become more overworked and overwhelmed by their new hybrid infrastructures.
In today’s climate, senior executives approach discussions about cyber risk with the expectation of hearing unfavorable news. Indeed, matters have escalated of late with the emergence of human-mimicking AI. We used to take comfort in the fact that at least Artificial Intelligence could not be creative like people could. But that was before generative AI came along and left us speechless — with delight or dread, depending on our day job. For security professionals, it is the latter because every new technology that arrives will eventually get exploited by threat actors. AI and its generative subspecies can make it easier to find vulnerabilities, which implies there will be a surge in the volume of zero-days. And GenAI can pump out convincing phishing content at a scale unreachable by human criminals.
But in a break with tradition, I offer good news. In the daily struggle with ransomware threats, the answer lies in the daily fundamentals of IT admin. Patch management is the keystone of cyber resilience. As each vulnerability becomes known and fixes are released, that dreaded countdown begins again. Whether threat actors have beaten vendors to the punch by publishing an exploit before the patch was released or not, organisations must be prepared to act strategically when fixes become available. It may be that a patch fixes an error that poses no risk to the enterprise, in which case patching would not have much impact on reducing cyber risk. Hence, organisations need to look at prioritising patching the assets that cause the most existential risk to the company, maximising their patch rate (a measure of how effectively vulnerabilities are addressed) and minimising their mean time to remediation (MTTR) for such ‘crown jewel’ assets.
Windows mean doors
The Qualys Threat Research Unit (TRU) uses these metrics often in anonymised studies of organisations’ cyber-readiness. Our 2023 Qualys TruRisk Research Report found that weaponised vulnerabilities are patched within 30.6 days in 57.7% of cases, whereas attackers typically publish exploits for the same flaws inside just 19.5 days. That 11-day window is where our concerns should be concentrated. It should spur us to revisit patch management and — if we have not already — to integrate it into our cybersecurity strategy so we can start to close our open doors to attackers.
If we imagine a graph of MTTR plotted against patch rate for every vulnerability, then we can imagine four quadrants, defined by combinations of ‘high’ or ‘low’ for our two metrics. Our sweet spot is in the bottom righthand corner, where patch rate is high and MTTR is low. We could call this quadrant, the ‘Optimal Security Zone’. If a vulnerability is in this zone, we are unfazed by it. It is low-risk because it is patched and resolved quickly. In the top right, we find that patch rate is still high, so we call this the ‘Vigilant Alert Zone’, but incidents take a longer time to remediate (high MTTR). But while this is a higher source of concern, it is less worrying than if a vulnerability falls in the bottom left quadrant — the ‘Underestimated Risk Zone’. Here, we find overlooked vulnerabilities (low patch rates) but unexpectedly short remediation times. These flaws can quickly become risks if left unaddressed. Finally, we come to our red-flag quadrant, the ‘Critical Attention Zone’ (top left), where vulnerabilities have low patch rates and take a long time to resolve.
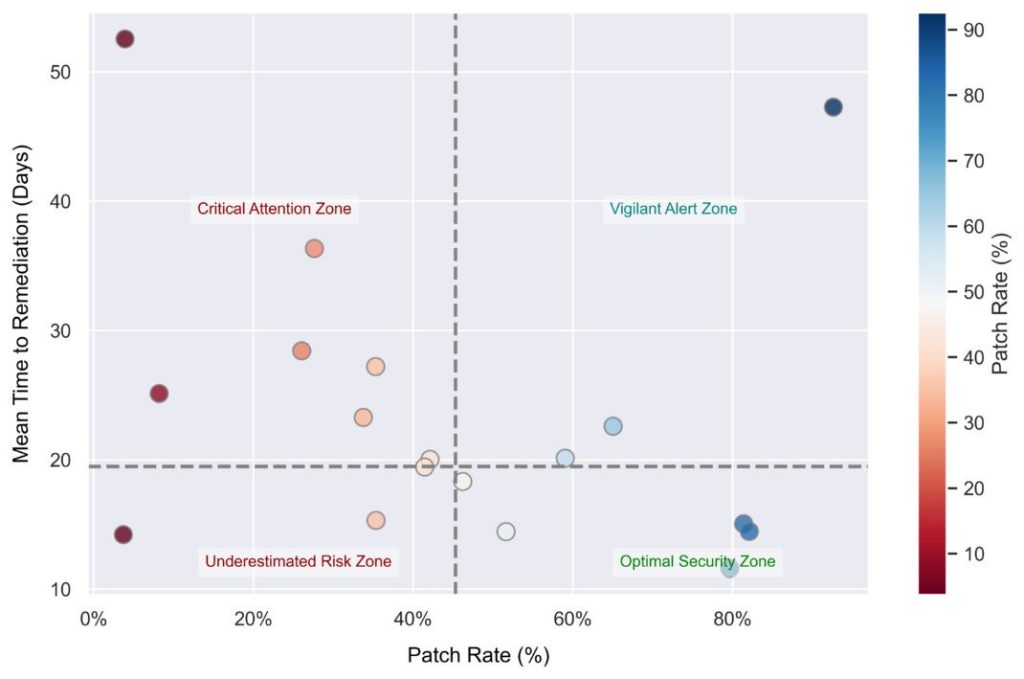
Combining metrics like this can give us important crossover information that allows us to triage our patch management effectively. By exploring the critical areas first, we can examine overlooked vulnerabilities and discover either that they pose little threat and are less of a source of concern, or that they could lead to a ransomware incident, in which case they become a top priority on our to-do list. With RansomOps groups now leveraging advanced automation tools, the importance of optimal patch management cannot be overstated. Ensuring that systems are updated and secure is critical to prevent potential vulnerabilities.
Action stations
GCC organisations should look to their vulnerability management strategy and determine an approach that is able to stand up to armies of threat actors, working as a unified industry, equipped with advanced AI, to disrupt, disable and damage the region’s innovative spirit.
We all need to make sure that our vulnerability gaps are closed and our defenses tightened against these malicious actors. Technical and business stakeholders must collaborate on crafting roadmaps that make sense to their operational uniqueness.
The hope remains that one day, cyber criminals, a persistent threat today, will be effectively countered by innovative security technologies. However, we must confront the fact that attackers are becoming more sophisticated, their campaigns are escalating in scope and the resources available for cybersecurity defense are often constrained.
The solution does not lie in an unknowable panacea, but in the day-to-day fundamentals — robust patch management that uses the four-quadrant principle and aims for the highest possible patch rate and the shortest possible resolution time. The top practitioners in any field — sports, business, the arts — will always extol the virtues of the fundamentals. If it works for them, then why not for us? So, let’s get back to basics and send the ransomware actor packing.



