As organisations attempt to optimise their business strategies, understanding threat intelligence has never been more important. Bert Skaletski, Resident CISO for EMEA, Proofpoint, tells Intelligent CISO about how Proofpoint’s State of Phish Report can help organisations better protect themselves in 2023 and beyond.

Why is threat intelligence important and why should CISOs integrate this into their business strategies?
The cybersecurity landscape is constantly evolving, and threat intelligence serves to collect information on attacker motives, exploit capabilities, malware code, infrastructure and resources. To protect businesses from threats, cybersecurity researchers continually seek out intelligence on the next potential attack. Hackers and threat intelligence researchers are still playing the proverbial cat-and-mouse game where researchers find and remediate threats and attackers find new ways to bypass defenses, thus incorporating threat intelligence into your cybersecurity strategy is crucial if you want to attempt to stay ahead of attackers. The Proofpoint Threat Hub is a great free resource for the latest threat intelligence.
The State of Phish Report revealed some of the biggest regional cyberthreats across 15 countries. What was it that surprised you the most about the results?
When you’ve worked in cybersecurity for a while one of the most surprising parts of the research that goes into State of the Phish is user awareness of cyberthreats – or the lack thereof. Even basic cyberthreats are still not well understood – more than a third of survey respondents cannot define ‘malware’, ‘phishing’ and ‘ransomware’. Also, nearly half (44%) of employees indicate they think an email is safe when it contains familiar branding, and 63% think an email address always corresponds to the matching website of the brand.
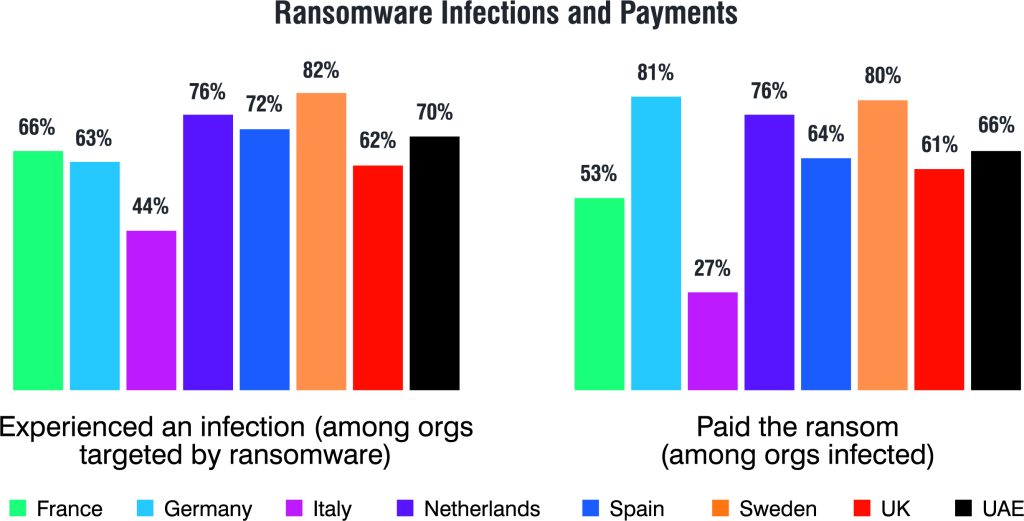
In addition, although ransomware is nothing new, it continues to wreak havoc globally. The report revealed that eight out of 10 UK organisations (82%) experienced an attempted ransomware attack in 2022 with 62% suffering a successful infection, and of those infected, just 33% of organisations were able to regain access to data after paying a ransom. Looking at this from an EMEA lens, there are some surprising differences. While Swedish organisations were the most likely to pay ransomware demands (80% vs. a 64% global average), UK organisations fared worse overall when compared to all 14 countries. Not only did they fail to get access to their data after payment (33% vs. 52%), but their cyberinsurance claims were denied most often (23% vs 7%).
What trends are shaping the future of cybercrime threat intelligence and how can organisations protect themselves?
There’s no question that organisations have experienced widespread cybersecurity challenges in the past year. While conventional and well-known threats such as email phishing and ransomware remain successful, many threat actors are shifting to newer techniques, lesser known to employees to increase their chances of a successful cyberattack. If an employee isn’t aware of certain threat tactics, or are able to identify them, they are more likely to fall victim to them.
These include telephone-oriented attack delivery and adversary-in-the-middle (AitM) phishing proxies that bypass multifactor authentication. These techniques have been used in targeted attacks for years, but 2022 saw them deployed at scale.
Over the past year, hundreds of thousands of telephone-oriented attack delivery (TOAD) and multi-factor authentication (MFA) bypass phishing messages were sent each day—ubiquitous enough to threaten nearly all organisations. At its peak, Proofpoint tracked more than 600,000 TOAD attacks—emails that incite recipients to initiate a direct conversation with attackers over telephone via bogus ‘call centres’—per day, and the number has been steadily rising since the technique first appeared in late 2021.
Insider threats are a growing concern for many regions. What are the pain points for organisations and how do the regions differ?
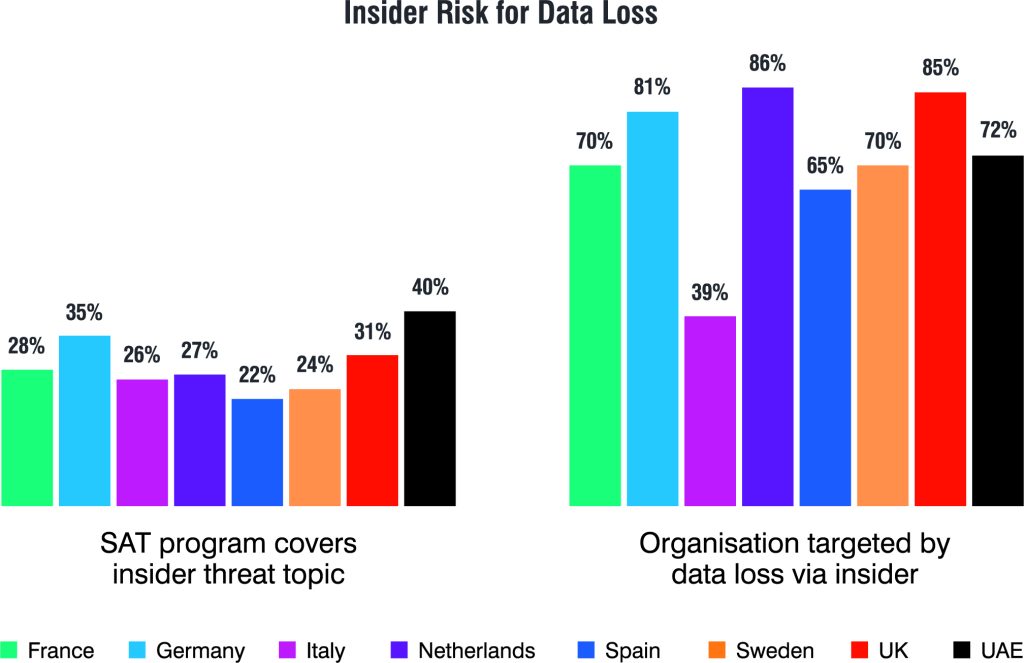
Insider threats make data protection more difficult for organisations. Also, recent job market trends like The Great Resignation have presented security challenges for global organisations, with 65% – on global average – reporting they have experienced data loss due to an insider’s action.
We are seeing the trend across all territories, but in different levels of severity. Across EMEA, an average of 71% of organisations lost data to insiders. What’s notable is the disconnect between the high level of attacks and the low average level of security awareness training, at 29%.
How is cybersecurity maturity across the world shaping how CISOs revise their current security strategies?
With so much variation between regions and industries, there is no one-size-fits-all cybersecurity strategy. CISOs need to consider an individual, tailored program, which corresponds with real-time events, related to their region, industry and company risk appetite. As threat actors constantly evolve their techniques, to new, unknown attacks, it’s difficult to state that every organisation has a fully robust cybersecurity strategy – which again, is why threat intelligence insights are so important.
How can companies create an individual security policy tailored to real life threats and user risks?
While threat actors are constantly homing in on new techniques, one thing will remain the same: they are targeting people, as opposed to infrastructure (on most occasions). Organisations must consider how they can tailor an individual cybersecurity strategy that incorporates people, process and technology.
When looking at the people part of this policy, organisations should consider the below:
Reduce complexity by asking the right questions.
• Who in my organisation is being attacked?
• Where are the current defensive gaps?
• What are my priorities to mitigate human risk?
Pair threat intelligence with organisation-wide security awareness education.
• Identify which users are most likely to be targeted and who is most likely to succumb.
• Match training content to threats currently circulating.
• Train people to recognise phishing using the lures targeting them.
Build a security culture that goes beyond training.
• Training is crucial but not singularly sufficient.
• A strong workplace security culture will encourage users to take information security more seriously in their personal lives.
• Measure the metrics that matter and respond with appropriate and fair remediation.
How can companies ensure employees are able to define basic concepts and terminology to build a security awareness culture?
To educate their users, and with the best intentions, many organisations provide one or two hours of security awareness training annually. But this limited approach lacks staying power. It doesn’t promote lasting changes in behaviour. And it doesn’t instill the kind of security mindset that can transform your biggest attack surface into a critical layer of defence.
What can we do better? The answer lies in developing a systematic, sustainable and customised security culture—one that pervades the organisation across all users and all digital activities. Worryingly, only 58% of UK organisations with a security awareness program train their entire workforce, and only 39% conduct phishing simulations—both critical components to building an effective security awareness program.
Most attacks target people before they target systems – what can CISOs do to improve their strategies for 2023 and beyond?
Our CISO team’s predictions all point to the same theme: organisations need to go back to the basics to ensure they are protecting their people and their data. Whatever weaknesses threat actors exploit in 2023 people will remain their favorite attack surface and data their desired prize, underscoring the importance of cyberhygiene and a holistic approach to defense strategies.
Taking a broader lens beyond individual organisations, we see a growing need for public and private sectors to come together to boost our resiliency. With cybersecurity emerging as a national security concern in recent years, our industry and the government must work collaboratively to address these pressing cybersecurity issues.



