More than 160 days after the last observed Emotet delivery via email, Proofpoint researchers have confirmed its return. More recently, they have observed Emotet delivering third-party payloads such as Qbot, The Trick, IcedID and Gootkit. Additionally, Emotet loads its modules for spamming, credential stealing, email harvesting and spreading on local networks.
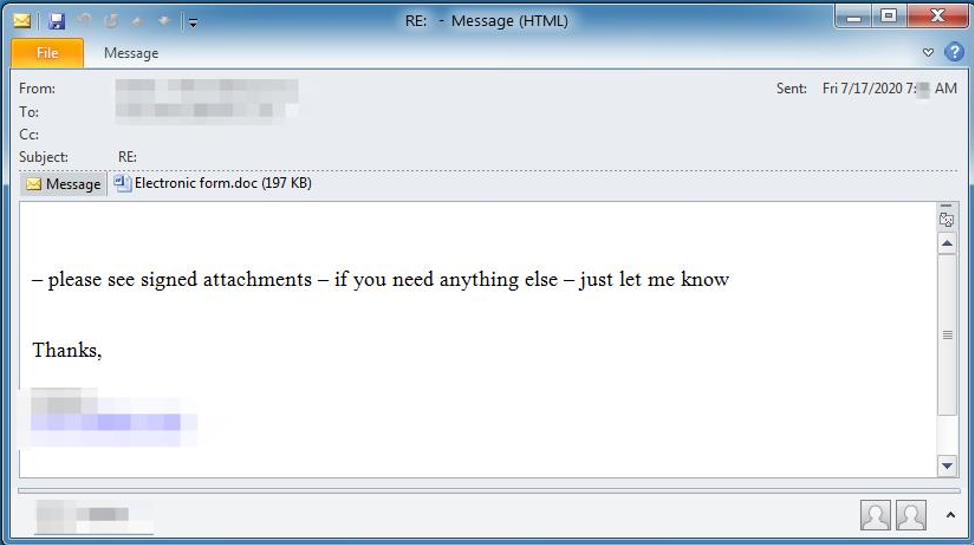
Proofpoint has observed nearly a quarter of a million Emotet messages sent on July 17, 2020, and the number continues to climb. The threat actor, TA542, appears to have targeted multiple verticals across the US and UK with English language lures. These messages contain malicious Microsoft Word attachments or URLs linking to Word documents, often pointing to compromised WordPress hosts.
Similar to lures observed previously, these are simple, with minimal customization. Subject lines like ‘RE:’, ‘Invoice #’ followed by a fake invoice number are commonly seen and often include the name of the organization being targeted.
Sherrod DeGrippo, Senior Director, Threat Research and Detection at Proofpoint, said: “Emotet’s infrastructure is test and metric-driven and is built to scale depending on what’s working. Hence, it is important that security teams continue to secure their email channel and educate users regarding the increased risks associated with potentially malicious email attachments to protect against this form of attack.”